Deception technology enables security teams to evolve from simple log aggregation and static detection use-cases to a proactive, low false-positive detection model, with deep analytics to convert data to information, and finally, heavily automated response mechanisms.
In summary, it arms security operations teams with many of the most desired capabilities of a next-gen SOC.
Here’s a low-down of how deception technology levels up your SOC:
1. Aligns With the ‘Assume Breach’ Approach
There were days (or were there?) where defenders could neatly divide their network into trusted and untrusted. Alas, networks are now more complex than ever and adversaries are ahead for the most part.
It’s no surprise then that the industry has moved to assuming that the environment is hostile, and is likely in various stages of compromise already.
This approach liberates defenders from having to try and plug every weakness (an impossible task!) to baselining and monitoring for compromise in progress.
If security teams have a good baseline and reliable telemetry, they can find even the most sophisticated attackers dwelling within the network.
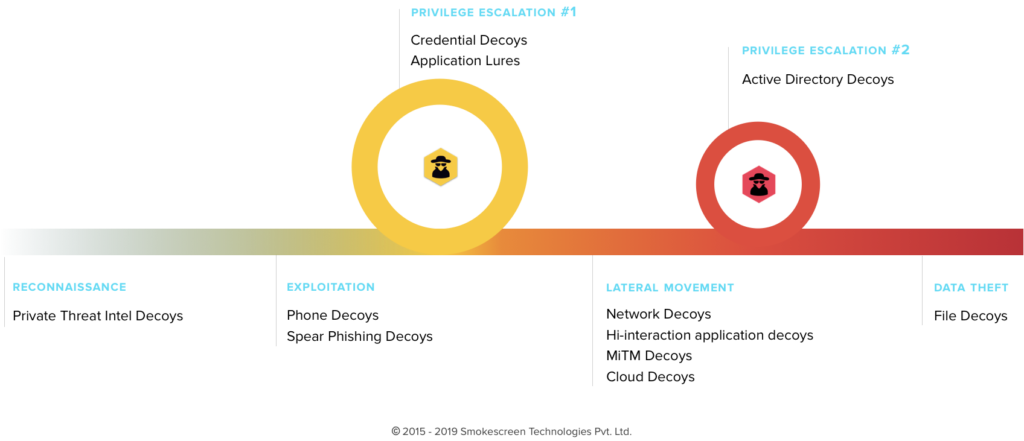
Deception technology already ‘assumes breach’. Decoys are placed on endpoints, in Active Directory, and on the network, in such a way that an attacker in progress will engage with these deceptive assets and reveal their presence.
2. Enables Active Defence
Deception is an ‘active defence’ strategy, designed to make the network hostile for attackers, and to shift the costs of remaining undetected onto them.
In contrast, static security monitoring use-cases fall out of date quickly, and cannot keep up with changing attacker tactics, thus making it easier for attackers to evade detection and dwell within the network for months or even years.
However, deception does not rely on static use-cases. By targeting the human intent behind an attack, as opposed to the tools, exploits, or techniques being used, deception-based defences can remain effective no matter what the bad guys try in the future.
This means that the modern SOC can stay agile and adaptive to new threats without having to wait to see them first. Deception can also be used by threat- hunters and incident responders to lay down traps both to find evil or dimension the spread of an on-going incident.
3. Low False Positives
Traditional SOCs have ‘cried wolf’ far too often. Even with significant tuning, finding the balance between too many alerts, and missing real incidents is extremely challenging and a constant process.
A reduction in the number of false positives automatically makes the security team more productive as they can focus on real threats instead of chasing down ghosts.
Deception technology has extremely low false positives because nobody should even interact with a decoy system, credential, or file. Any interaction is worthy of investigation, and can even trigger an orchestrated response. This means that the SOC can reduce the number of alerts to only the ones that matter.
4. Data Analytics and Threat Intelligence
Most data analytics focuses on ‘collecting everything’ and then trying to make sense of the data. Security is not necessarily a big-data problem, it’s more of a ‘good-data’ problem.
Since deception systems only see anomalous or malicious traffic, data-analytics can be applied to better understand the threats within the network instead of hunting for a needle in a haystack (or ElasticSearch DB!).
This also means that the SOC can move from consuming static, external threat intelligence (which is not specific, and often stale) to creating its own threat intelligence and IOCs that are more relevant to the business, and can better inform future defences.
5. Orchestrated Response
In order to deal with threats at wire-speed, you need orchestrated response mechanisms. However, the challenge is to find orchestration triggers that are so reliable that a human being does not have to validate them before the response is actually fired. Failing to do so can mean that response actions trigger on false positives, which can lead to disruption of legitimate business activity.
With low false positives and built-in orchestration and integration capabilities, a deception platform can enable ‘continuous response’, reliably detecting compromised assets and users within the network, and investigating, containing or eradicating the threat automatically, without the need for human intervention.
6. Detects Insider Threats
While security teams have typically focused more on external adversaries, the insider with legitimate access is far harder to tackle. They often have detailed knowledge of the security mechanisms in place and can tailor their malicious intent to look completely benign.
Deception can detect insiders seeking out data on high-value target personnel, searching for systems they should not access, or copying and opening data that they are not authorised to. It also injects an element of unpredictability; deception deployments are invisible to normal users, and the placement of decoys is known only to a limited trusted circle, so the insider will either not know of the existence or the placement of the deception. This also serves as a deterrent against casual fraud or misplaced inquisitiveness by internal employees.
Deception is a crucial component of the modern SOC. The use of adversarial thinking against the attacker changes the game for defenders, letting them ‘punch above their weight’ against sophisticated adversaries.
Want to learn how Smokescreen’s deception platform fits into your SOC? Download the whitepaper.
Continue Reading
Finding active defense opportunities in a pentest report
Pentest reports tell a story. By asking why a pentester made certain choices, you can find opportunities to influence attacker behavior and actively defend your network.By Sudarshan PisupatiFour MITRE Shield Techniques You Can Implement in 2021
For free, of course. At this point, I’m positive that you’ve heard of MITRE Shield. It’s a new active defense knowledge base released by MITRE – stuff they’ve been implementing for over a decade to engage adversaries and derail attacks. They’ve opened it up to everyone, and for the first time perhaps, the infosec community […]By Sudarshan PisupatiActive Defense – Incident Response’s New Best Friend
Active defense provides defenders with a shared vocabulary and framework for actively dealing with threats instead of passively reacting to them.By Sudarshan Pisupati
- Detect zero-days, APTs, and insider threats
- 10x the detection capabilities with 1/2 the team
- Get started in minutes, fully functional in hours
