Resources
Comprehensive insights on deception technology, active defence, and how to beat adversaries at their own game.
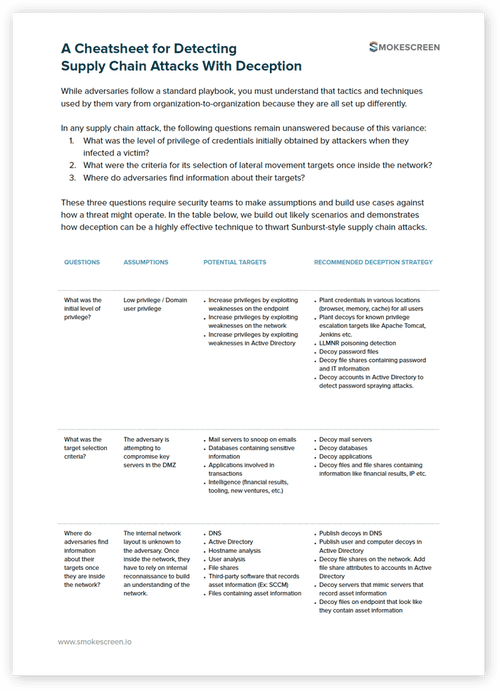
- WhitepaperDetecting Supply Chain Attacks With DeceptionInside You’ll Find A reference guide for making assumptions and building a deception-based defense strategy to thwart supply chain attacks. Three questions that go unanswered in a supply chain attack and can inform your ability to defend against it. The different assumptions you can make based on these questions to build out a defense plan. […]
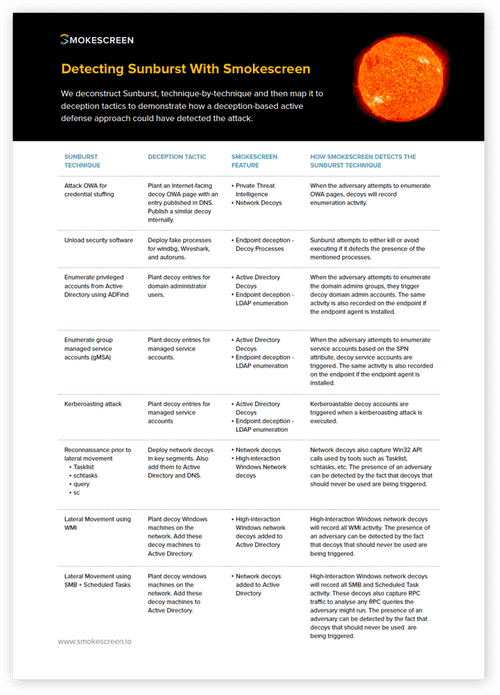
- WhitepaperDetecting Sunburst With SmokescreenInside You’ll Find A technique-by-technique deconstruction of the Sunburst attack mapped to deception tactics can detect the techniques. Perimeter and network decoys that detect credential stuffing attacks on OWA pages. Active Directory and endpoint decoys that detect enumeration of privileged accounts, managed service accounts, and kerberoasting. Network and high-interaction Windows decoys that detect reconnaissance prior […]
- WhitepaperDefending Against Sunburst-Style Supply Chain Attacks With DeceptionInside You’ll Find A blueprint for understanding how Sunburst-style supply chain attacks work and how you can thwart them with deception-based defenses. The anatomy of supply chain attacks with examples to help inform your thinking about them. A mental model that provides some guidance on defending against supply chain attacks. A technique-by-technique teardown of Sunburst […]
- Case StudyCreating Private Threat Intelligence With Deception Ahead of a Business LaunchInside You’ll Find An account of how Smokescreen enabled one of the world’s largest banks to build a private threat intelligence program ahead of a new business launch. Why the company chose Smokescreen to gather intelligence and create a threat model before launching a new business line. How we created a decoy replica of the […]
- WhitepaperAn Attacker’s View of a Work From Home WorldInside You’ll Find A blueprint of how attackers are laying siege to a perimeter-less world and recommendations on what you can do. An analysis of 500,000+ decoy interactions showing how attackers are approaching a perimeter-less world. The three paradigm shifts of a WFH architecture – Remote access services, your employees’ home network, and lean security […]
- WhitepaperAdopting the MITRE Shield Framework With SmokescreenInside You’ll Find A detailed mapping of all the active defense techniques in MITRE Shield to Smokescreen’s deception platform. We cover: An introduction to active defense, MITRE Shield, and how it helps CISOs adopt active defense for their security program. Mapping of the MITRE Shield matrix to the Smokescreen platform categorized by the use cases […]
- WhitepaperThreat Detection with Deception TechnologyInside You’ll Find A deep dive into what deception technology is, how it works, its use cases, and how it augments your security controls. We cover: What is deception and how it’s a fundamentally different/active approach to security. What kind of businesses and security teams benefit the most from deception-based defenses. Using deception to detect […]
- WhitepaperActively Defending Air-Gapped Networks With DeceptionInside You’ll Find An overview of how air-gapped networks are set up, their limitations, and why deception is a viable approach to detecting threats in them. The anatomy of air-gapped networks and what makes them hard to defend post-breach. The passive nature of air-gapped networks and three reasons they get hacked despite being seemingly impenetrable. […]
- Case StudyBuilding Visibility in Industrial Networks with DeceptionLearn how Smokescreen helped a large energy company with a complex industrial control systems infrastructure build visibility along with threat detection capabilities without any impact on availability.
- WhitepaperMitigating Cyber Risks in IT Services With DeceptionLearn how Smokescreen helped an NYSE-listed business process management company detect that their critical identity and access management servers had been made remotely accessible.
- Case StudyMitigating 3rd Party Risks for ATMs With DeceptionLearn how Smokescreen’s deception platform helped one of the world’s largest banks detect and contain an ATM network breach originating from a 3rd party managed vendor network.
- WhitepaperThe Business Case for Detecting Targeted Cyber AttacksTraditional cybersecurity defences cannot stop targeted attacks that are tailor-made for each victim company. This whitepaper examines why businesses need to defend against them.
- WhitepaperAdversarial-Driven Security for SCADA / ICS SystemsThis white-paper explains how attackers target industrial control systems in the real world, and describes an attack pattern driven approach to defending these systems that actually works.
- WhitepaperDeception Technology for the Next-Gen SOCDeception is great on its own but when combined with your existing security stack, it becomes a force-multiplier. Learn how Smokescreen’s deception platform fits into your SOC.
- WhitepaperA Guide to Evaluating Deception TechnologyAre you evaluating deception solutions? Looking to run a PoC? This guide will help you understand what differentiates effective deception platforms from commodity solutions.
- Competitive ComparisonDeception Technology vs Network Traffic AnalysisThis whitepaper compares how network traffic analysis tools and deception platforms meet the goals of targeted threat detection, high network visibility, and minimised response time.
- Competitive ComparisonSmokescreen vs Fidelis DeceptionThis comparison examines how Smokescreen compares with Fidelis Deception on parameters like detection capabilities, deception realism, and ease of use and deployment.
- Competitive ComparisonSmokescreen vs Attivo NetworksDeception platforms must be highly secure, easy to use, and near impossible to fingerprint. Learn how Smokescreen IllusionBLACK compares with Attivo Technologies on these parameters.
- Competitive ComparisonDeception Technology vs UEBAOrganisations want to detect serious threats with confidence and respond to them swiftly. This whitepaper compares how UEBA and deception solutions meet these goals.
- Competitive ComparisonSmokescreen vs Symantec DeceptionThis competitve comparison explores how Smokescreen stacks up against Symantec Deception on parameters like detection capabilities, deception realism, and ease of use and deployment.
- Industry SolutionDeception Technology for Banking and FinanceBanking and Finance networks are a prime target for financially motivated attackers. Learn how Smokescreen enables 26 of the world’s largest banks to detect targeted threats.
- Industry SolutionDeception Technology for SCADA / ICS SystemsIndustrial networks require high availability and are therefore hard to secure. Learn how Smokescreen IllusionBLACK helps build visibility in these networks and detect advanced threats.
- Industry SolutionDeception Technology for the Healthcare IndustryThe healthcare industry is the #1 target of ransomware attacks. Hackers target patient data and life saving devices and equipments. Learn how deception technology stops them.
- Case StudyDeception Technology at the World’s Fastest Stock ExchangeLearn how, BSE, the world’s fastest stock exchange, uses Smokescreen’s deception technology to detect advanced threats and cut down its time to know and time to respond metrics.
- WhitepaperDetecting Supply Chain Attacks With DeceptionInside You’ll Find A reference guide for making assumptions and building a deception-based defense strategy to thwart supply chain attacks. Three questions that go unanswered in a supply chain attack and can inform your ability to defend against it. The different assumptions you can make based on these questions to build out a defense plan. […]
- WhitepaperDetecting Sunburst With SmokescreenInside You’ll Find A technique-by-technique deconstruction of the Sunburst attack mapped to deception tactics can detect the techniques. Perimeter and network decoys that detect credential stuffing attacks on OWA pages. Active Directory and endpoint decoys that detect enumeration of privileged accounts, managed service accounts, and kerberoasting. Network and high-interaction Windows decoys that detect reconnaissance prior […]
- WhitepaperDefending Against Sunburst-Style Supply Chain Attacks With DeceptionInside You’ll Find A blueprint for understanding how Sunburst-style supply chain attacks work and how you can thwart them with deception-based defenses. The anatomy of supply chain attacks with examples to help inform your thinking about them. A mental model that provides some guidance on defending against supply chain attacks. A technique-by-technique teardown of Sunburst […]
- WhitepaperAn Attacker’s View of a Work From Home WorldInside You’ll Find A blueprint of how attackers are laying siege to a perimeter-less world and recommendations on what you can do. An analysis of 500,000+ decoy interactions showing how attackers are approaching a perimeter-less world. The three paradigm shifts of a WFH architecture – Remote access services, your employees’ home network, and lean security […]
- WhitepaperAdopting the MITRE Shield Framework With SmokescreenInside You’ll Find A detailed mapping of all the active defense techniques in MITRE Shield to Smokescreen’s deception platform. We cover: An introduction to active defense, MITRE Shield, and how it helps CISOs adopt active defense for their security program. Mapping of the MITRE Shield matrix to the Smokescreen platform categorized by the use cases […]
- WhitepaperThreat Detection with Deception TechnologyInside You’ll Find A deep dive into what deception technology is, how it works, its use cases, and how it augments your security controls. We cover: What is deception and how it’s a fundamentally different/active approach to security. What kind of businesses and security teams benefit the most from deception-based defenses. Using deception to detect […]
- WhitepaperActively Defending Air-Gapped Networks With DeceptionInside You’ll Find An overview of how air-gapped networks are set up, their limitations, and why deception is a viable approach to detecting threats in them. The anatomy of air-gapped networks and what makes them hard to defend post-breach. The passive nature of air-gapped networks and three reasons they get hacked despite being seemingly impenetrable. […]
- WhitepaperMitigating Cyber Risks in IT Services With DeceptionLearn how Smokescreen helped an NYSE-listed business process management company detect that their critical identity and access management servers had been made remotely accessible.
- WhitepaperThe Business Case for Detecting Targeted Cyber AttacksTraditional cybersecurity defences cannot stop targeted attacks that are tailor-made for each victim company. This whitepaper examines why businesses need to defend against them.
- WhitepaperAdversarial-Driven Security for SCADA / ICS SystemsThis white-paper explains how attackers target industrial control systems in the real world, and describes an attack pattern driven approach to defending these systems that actually works.
- WhitepaperDeception Technology for the Next-Gen SOCDeception is great on its own but when combined with your existing security stack, it becomes a force-multiplier. Learn how Smokescreen’s deception platform fits into your SOC.
- WhitepaperA Guide to Evaluating Deception TechnologyAre you evaluating deception solutions? Looking to run a PoC? This guide will help you understand what differentiates effective deception platforms from commodity solutions.
- Competitive ComparisonDeception Technology vs Network Traffic AnalysisThis whitepaper compares how network traffic analysis tools and deception platforms meet the goals of targeted threat detection, high network visibility, and minimised response time.
- Competitive ComparisonSmokescreen vs Fidelis DeceptionThis comparison examines how Smokescreen compares with Fidelis Deception on parameters like detection capabilities, deception realism, and ease of use and deployment.
- Competitive ComparisonSmokescreen vs Attivo NetworksDeception platforms must be highly secure, easy to use, and near impossible to fingerprint. Learn how Smokescreen IllusionBLACK compares with Attivo Technologies on these parameters.
- Competitive ComparisonDeception Technology vs UEBAOrganisations want to detect serious threats with confidence and respond to them swiftly. This whitepaper compares how UEBA and deception solutions meet these goals.
- Competitive ComparisonSmokescreen vs Symantec DeceptionThis competitve comparison explores how Smokescreen stacks up against Symantec Deception on parameters like detection capabilities, deception realism, and ease of use and deployment.
- Industry SolutionDeception Technology for Banking and FinanceBanking and Finance networks are a prime target for financially motivated attackers. Learn how Smokescreen enables 26 of the world’s largest banks to detect targeted threats.
- Industry SolutionDeception Technology for SCADA / ICS SystemsIndustrial networks require high availability and are therefore hard to secure. Learn how Smokescreen IllusionBLACK helps build visibility in these networks and detect advanced threats.
- Industry SolutionDeception Technology for the Healthcare IndustryThe healthcare industry is the #1 target of ransomware attacks. Hackers target patient data and life saving devices and equipments. Learn how deception technology stops them.
- Case StudyCreating Private Threat Intelligence With Deception Ahead of a Business LaunchInside You’ll Find An account of how Smokescreen enabled one of the world’s largest banks to build a private threat intelligence program ahead of a new business launch. Why the company chose Smokescreen to gather intelligence and create a threat model before launching a new business line. How we created a decoy replica of the […]
- Case StudyBuilding Visibility in Industrial Networks with DeceptionLearn how Smokescreen helped a large energy company with a complex industrial control systems infrastructure build visibility along with threat detection capabilities without any impact on availability.
- Case StudyMitigating 3rd Party Risks for ATMs With DeceptionLearn how Smokescreen’s deception platform helped one of the world’s largest banks detect and contain an ATM network breach originating from a 3rd party managed vendor network.
- Case StudyDeception Technology at the World’s Fastest Stock ExchangeLearn how, BSE, the world’s fastest stock exchange, uses Smokescreen’s deception technology to detect advanced threats and cut down its time to know and time to respond metrics.
Have you tried out IllusionBLACK yet?
- Detect zero-days, APTs, and insider threats
- 10x the detection capabilities with 1/2 the team
- Get started in minutes, fully functional in hours