Deception technology is all the rage these days. From mature security teams at large enterprises to lean teams at mid-market companies, almost everyone is beginning to see the benefits of early threat detection. While there are clear merits, there is a lot of vendor-speak out there that might make it hard for you to evaluate if deception is the right approach for your security strategy.
With this guide, we intend to answer some questions around what the technology is, who it’s for, what it’s capable of doing (and not doing), key use cases, and advantages. We’re going to keep it simple but go fairly deep where necessary. So grab a cup of coffee (or beer depending on when you’re reading this) and strap in.
What is Deception Technology?
Let’s start with the basic definition. Deception technology is a simple but effective approach to building security defences that detect threats early with low false positives and minimal performance impact on the network. The technology works by creating decoys – realistic-but-fake assets (domains, databases, servers, applications, files, credentials, cookies, sessions, and more) that are deployed in your network alongside legitimate assets. For an attacker who has breached the network, there is no way to differentiate the fake from the real. The moment they interact with a decoy, a silent alarm is raised while the systems collect information on the attacker’s actions and intent.
Understanding Deception
Modern-day deception technology-based cybersecurity defences borrow heavily from proven military deception principles employed by the likes of Chanakya, Sun Tzu, Napoleon, and Genghis Khan to conquer continents by use of deceit, camouflage, and subterfuge. The most famous example of military deception perhaps is Operation Fortitude which was devised by the Allied forces to mislead the German high command as to the location of the invasion eventually leading to the Normandy landings.
In the context of cybersecurity, defenders use decoys and lures to mislead attackers into believing that they have a foothold in the network and revealing themselves. The beauty of this approach lies in its simplicity.
Winning a Rigged Game with Deception
Picture two adversaries with comparable capabilities but differing goals facing off against each other. The odds of either of them winning are usually at a coin toss. What if one of the two had the benefit of speed, flexibility, and targeted information? It’s no contest. The speedier, more nimble of the adversaries will usually outcompete their opponent. Even so, the latter has greater strength and access to more information. Why? Because the opponent with more information falls into ‘analysis paralysis’. They have so much information that analysing all of it becomes infeasible and some information must be prioritised over the rest. This is how adversaries lacking in strength usually win an adversarial contest.
Something very similar happens in cybersecurity. Consider for a minute how things have played out over the past couple of decades.
Attacker: Let’s play a game with some simple rules. I’ll try to access your information or other resources. If I’m successful once, I win.
Defender: Sounds fair.
Attacker: If you prevent me from being able to reach my target at any time including otherwise rough or busy days, after-hours, on weekends and holidays… you win.
Defender: …
No wonder we’re losing. It’s a rigged game. As a defender, you need to be right 100% of the time. The attacker just has to be right once. Thankfully, deception flips the table by placing the burden of success on the attackers instead. Once you populate your network with decoys, adversaries need to carry out a flawless attack without interacting with any deceptive assets, triggering any detection controls, or prompting other defensive actions, to succeed in their attack. In other words, the attacker now needs to be right 100% of the time, while a single mistake hands the defenders a win.
What Attacks Can Deception Technology Detect?
Deception technology is attack-vector-agnostic. It only ever looks at the intent of the adversary to detect attacks. No legitimate user has any business accessing a decoy system, file or application. Therefore, by design, any interaction with a decoy is suspicious at a minimum and malicious at worst. Since deception-based defences do not depend on signatures or heuristics for detection, they are able to detect virtually any attack including APTs, zero-days, reconnaissance, lateral movement, malwareless attacks, social engineering, man-in-the-middle attacks, and ransomware in real-time.
Is Deception Technology Effective Against All Adversaries?
Yes and no. Against the vast majority of adversaries, deception is extremely effective because it leverages the fact that they do not know everything about the network they’re trying to move around. Since decoys are essentially just another asset in the network and their strength is functional and not technical, differentiating them from legitimate assets is virtually impossible.
Further, by injecting fake records in a user’s browser history, password manager, and other common points of internal reconnaissance, the attacker can be deceived about functional uses of decoys, making them appear like they are either regularly-used assets – indicating they’re likely useful and can be used by the attacker to move laterally to what appears to be a valuable target – or an infrequently-used but valuable asset – indicating they can be used to access privileged and/or critical information.
However, deception can lose some of its efficacy against attackers with extensive knowledge of the various components needed for a successful attack and their functional use. A malicious member of the team responsible for a deception deployment, for instance, is a prime candidate for such activity. Even here, though, deception can be extremely effective when coupled with other tools in your security stack. Monitoring access to privileged and sensitive resources through other solutions such as PIMs and DLPs goes a long way towards covering these blind spots in a deception program. This fits right into a defence-in-depth strategy.
Who is it for?
It’s assumed that deception is a capability deployed only by highly mature security organizations. While this was largely true five years ago, we have identified that the large mid-market enterprise and smaller companies also find the technology extremely attractive. Deception is becoming a mainstream capability across markets. Here’s how:
The Security 1%-ers
Forward-leaning, big-budget, large-security-team-type organisations benefit from deception as an optimisation across their threat detection, internal threat intelligence creation, and response capabilities.
Large customers look to detect better, more advanced threats with deception and leverage the low false-positive alerts either for proactive threat-hunting, or integrated response through enforcement technologies that they have already invested in. This market segment has led the way for deception being more broadly adopted.
The Mid-market Enterprise
The mid-market CISO is faced with a conundrum — Her security team and budget are small, but she still has a significant threat and risk perception (perhaps she’s in an industry without compliance regulations driving investment).
She’s got some basic security hygiene in place but needs to do something to detect more serious threats. Her wish list from a solution is:
- Fast to get going – a quick win today v/s perfection tomorrow
- Easy to use and low maintenance given her small internal security team
- Not a point solution, as she can’t invest in multiple technologies
- Wide coverage for areas like cloud and IoT
Deception perfectly checks all the boxes above for her, letting her quickly start punching above her weight when it comes to more advanced, targeted threats.
What are the Advantages of Deception Technology?
When we launched IllusionBLACK in 2015, our CEO Sahir Hidayatullah, wrote a manifesto outlining the key advantages of deception technology. 5 years and 4 generations of deception platform later, those advantages still hold.
1. Improved Threat Detection
In anti-submarine warfare, the sighting of a periscope breaking the water is an unambiguous indicator of an imminent threat. We believe deception alerts are very similar, and term them ‘periscope events’ — a behavior that, when detected, clearly indicates that an attacker is in the network.
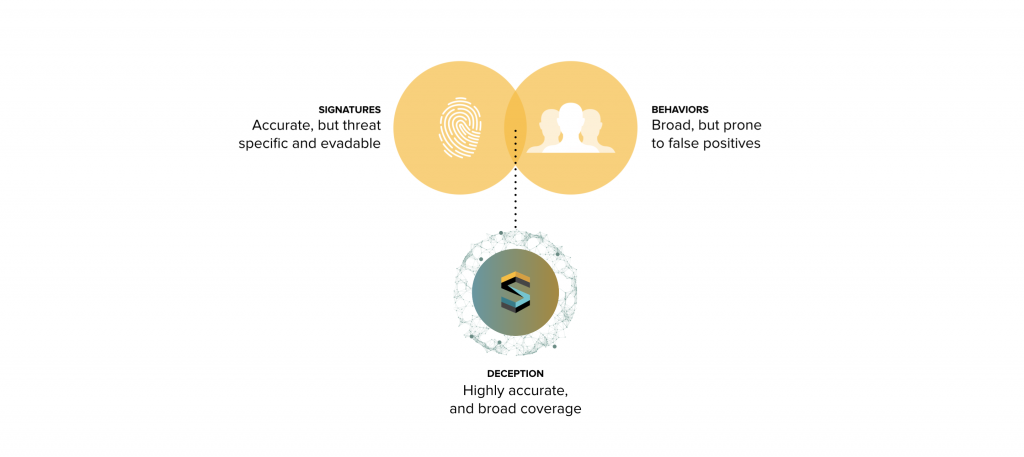
If you place detection classes on a scale of accuracy, at one extreme you have:
- Signature-based detection, which is highly accurate but very threat specific, (such as the propeller signature of a specific submarine).
- On the other extreme you have behaviors / heuristics which have broad threat coverage, but more prone to false positives (such as a radar contact that may be a submarine or a shoal of fish).
Deception’s periscope events are the middle ground — highly accurate, but with broad threat coverage (we can broadly detect any type of submarine with extremely low false positives).
2. Business Risk Awareness
Most security controls are not aware of current business risks (your antivirus does not know or care that you’re going through an M&A). However, deception is intrinsically aligned with the current business threat perception. For example, if a company is launching a new product, it can create deception around that product launch, aligning security controls tightly to areas where the organisation perceives risk.
3. Greater Coverage
Since deception is a detection class, it can be applied broadly horizontally across the enterprise, including environments that are often neglected blindspots. For example, deception can detect threats at the perimeter, the endpoint, the network, Active Directory, and application layers, as well as offer coverage to more neglected environments such as SCADA/ICS, IoT, and cloud.
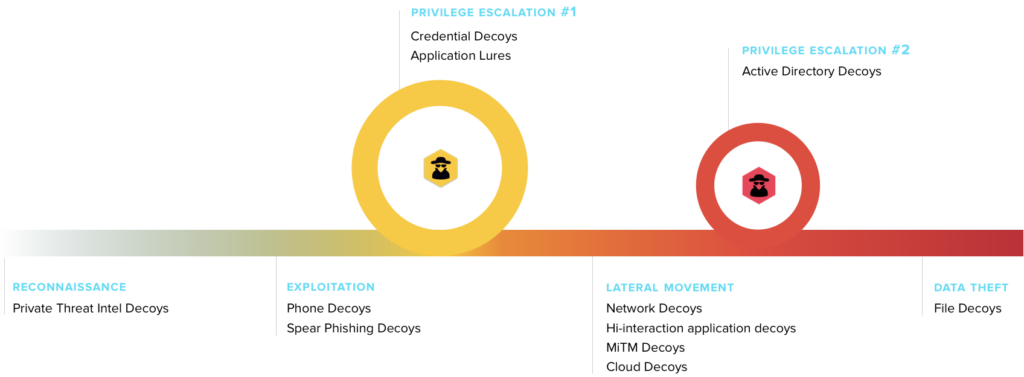
Unlike point solutions, deception also covers the entire kill-chain; from pre-attack reconnaissance to exploitation, privilege escalation, lateral movement, and data-theft / destruction.
4. Extremely Low False Positives
False positives cripple security team productivity and drag both IT and security teams through convoluted triage workflows. Often, the process of trying to validate the alert is more time consuming than the actual remediation measure.
Deception has an intrinsic low false-positive property — nobody should open a decoy file, log in to a decoy application, use a decoy credential, or scan a decoy server. However, the alerts are also far more contextual; giving insight into the attacker’s intent (“they went for the R&D information, not the financial systems”).
Most behavior-based systems try to establish a normal baseline and then classify any activity above the baseline as anomalous, this leads to a number of false positives. Deception establishes a zero-activity normal baseline, where any activity at all is worthy of investigation.
It also gives detailed IOCs (indicators of compromise). Everything that happens on a decoy is considered evil; so analysts don’t need to weed through the data to segregate legitimate user activity and forensically relevant artifacts. Not only can you detect more reliably, but you can ‘know your enemy’ far better.
You can also use deception to qualify medium or ‘warm’ alerts from other platforms. For example, a UEBA system may generate a medium risk score for a user’s behavior, leaving the analyst in no man’s land — “is this a threat, or a false positive?” Dynamic deployment of deception on and around that user’s environment may result in a higher-order detection if the attack is real.
Ring-fencing potential problem areas in this manner is also exceptionally useful during incident response in environments where the available logging is limited, but a rapid increase in visibility is required. If the DMZ may be compromised, lay down deception and watch for privilege escalation or lateral movement detection while the root cause of the compromise is being investigated. This can help answer two of the most fundamental questions in incident response, “how far in did they get, and are they still in?”.
5. Orchestrated Response
Orchestrated / automated response is most useful only when the trigger event is 100% certain. While plenty of orchestration tooling is being built (like shovels during the gold rush), not many real-world transformational orchestration use cases exist because there are very few alerts that are 100% certain. The ones that are, typically don’t require orchestration, because the products that generate them already contain remedial capabilities (for example, an antivirus detection quarantining a file).
Deception alerts are highly certain, contextual, and real-time, affording opportunities for security teams to orchestrate more complex and invasive scenarios (for example, use of a decoy credential can result in automatic redirection of the compromised asset into a decoy environment, while disabling the logged-on user’s account and access in the real environment).
In terms of containment / response use cases, deception alerts can integrate with:
- Network Access Control – Quarantine a compromised asset
- Web gateways – Disable the compromised asset’s Internet access, block phishing sites identified by email decoys.
- Endpoint protection – Kill a suspicious process or quarantine the endpoint
- EDR – Identify and block IOCs on all other endpoints
- Directory Services / Identity and Access Management – Disable the user’s account, change a password, and enable/enforce two-factor authentication
- Firewalls – Dynamically deny access to network segments
Since deception alerts are contextual, the response can also target the appropriate application. For example, if an attacker targets a decoy SWIFT server in a banking environment, the user’s account can be disabled for the real SWIFT server.
What Are the Key Use Cases of Deception Technology
Deception is being used to detect threats across the kill-chain starting with reconnaissance going all the way up to data theft. Broadly, we see three key use cases.
1. Perimeter Deception Defence
At a time when it’s possible to scan all IPv4 IPs in under an hour, monitoring all inbound connections – even just the unusual ones – becomes like drinking from the proverbial fire hose. With VMs available in the cloud within minutes, the noise comes not just from suspicious visitors to a page or from adversaries targeting the organisation, but from almost anyone that can create a cloud account and run a script or two.
Security isn’t a big data problem so much as a good data problem.
Setting up deceptive public-facing assets, if done right, can drastically simplify this problem and give you actionable telemetry on who’s targeting you. This is different from simply setting up a traditional honeypot with a number of open ports on a public IP. Such a setup is going to generate noisy alerts as everything from Google and Shodan to scripts for college research projects trying to connect to these honeypots. Instead, deploying decoys that mimic beta/staging applications can create high-confidence alerts telling you that an attacker is attempting to reach specific public-facing (but unannounced) infrastructure. Irrespective of their reason and methodology for doing so – including scripts set up to search for such infrastructure belonging to specific organisations, the alerts produced become a high-confidence indicator of intent to locate sensitive infrastructure belonging to your organisation.
These alerts become useful pivot points to check for other activity in the valuable but voluminous logs from the WAF (Web Application Firewall) and other sources. For example, other interactions by the source attempting to access public-facing decoys can be looked into and the source optionally blocked. If successful login attempts are discovered, resetting the user’s credentials and enabling 2FA (Two Factor Authentication) for the account are common first steps for a containment… You get the idea.
2. Network Deception Defence
Barring insider threats, once attackers gain a foothold in an organisation, they’re like a new employee on day one except for the onboarding – they have a very broad sense of the objective they need to achieve, but no information on the relative location of the things they need or how to get there.
A strategically deployed set of decoy internal servers and workstations play well here, being available as targets to the attacker. However, simply deploying decoys leaves the odds of them being targeted at not much better than random chance. Effective network deception requires the decoys to be placed in the various locations an attacker might peruse to identify targets; better still if they can be made to look not just like valuable assets on the network, but systems that the appropriate legitimate users interact with to perform their tasks.
Regular users know the hostnames or network locations of the databases they need to administer, the document servers they need to pull files from, the hosts they must remote into. Even forgetful users that connect to a couple of incorrect hosts in the course of looking for the one they want are unlikely to continue once they can see that they have connected to a different host than the one they intended to connect to.
An attacker, on the other hand, often has something of value to glean from connecting to a different system than the one they seek to target. This results in different behavior from a regular user, making attacker interactions with decoys easy to differentiate from a user that mistyped an IP. As with other types of deception, such alerts then make for great points to begin investigations from.
3. Endpoint Deception Defence
Consider your usage of the file system on your machine. More often than not, you probably know which file you want and where it’s located. For folks that deal with a large number of local files, you may search through the file system using some keywords you know to be associated with or present in the file you’re looking for.
However, if a decoy file is placed on your system, it’s unlikely to affect any tasks you need to perform, particularly if you know it’s a decoy. To an attacker, though, a file that appears to have legitimate and valuable content, and looks like it is accessed by the user, is a candidate for exfiltration.
Coupled with fake processes, and breadcrumbs pointing to decoy workstations/servers posing as legitimate systems accessed by the user, endpoint deception can be put to use to detect not just behavior that would be suspicious on the network, but also behavior that would be the norm on the network but has no legitimate place on a particular endpoint at a particular time.
Even a malicious insider who might be familiar with weaknesses in existing defences doesn’t have extensive knowledge of every valuable file on other endpoints. Additionally, since the goal of many attacks is data theft, theft of decoy files becomes a particularly high priority signal because it indicates an attacker may be close to accomplishing their goal – after all, an attacker stealing decoy files is likely to also be stealing real ones.
How does Deception Technology Augment Your Security Stack?
Deception technology is a “force multiplier” for a number of existing capabilities that organisations may already have implemented. Here are some examples:
Deception + Endpoint Detection & Response
Endpoint detection can be significantly improved with deception. An attacker using decoy credentials stored in memory, following a decoy SSH or RDP session, or trying to escalate privileges by exploiting a decoy running process provides extremely reliable indicators of malicious host-based activity. The EDR can ‘fill in the blanks’ into what happened before (which processes ran, what other network connections were created etc.)
Deception + User Entity and Behavior Analytics
User Entity and Behavior Analytics (UEBA) systems are prone to false positives and data paralysis, especially in larger, geographically disparate networks where analysts may not have the context to validate an alert (Eric in the Paris security team doesn’t know why Nakamura san is uploading a lot of data in Tokyo).
However, the UEBA system can provide excellent enrichment to a deception alert, fleshing out the user backstory. For example, if a decoy file is copied and the user is suddenly logging in outside of office hours concurrently from two places, the detection is very likely to be real.
Deception + Sandboxes
Sandboxing was deception 1.0, focused on convincing malware to detonate and reveal its cards. Modern deception is sandboxing for the human attacker. By providing a wider virtual ‘attack surface’, and a believable environment for them to progress their attack, higher-order forensics can be developed.
Deception + Threat Intelligence
Many threat intelligence services offer dumps of malware hashes, domains or IPs that rapidly go stale or are devoid of context (“block these 5000 IPs because they’re from China”). The commercial ramp-up to more specific threat intelligence is significant, and often only consumable by extremely mature security organisations.
While deception is typically seen as a behind-the-firewall capability, it is possible to deploy Internet-facing decoys that only engage with targeted threats against a named organization. These ‘private threat intelligence’ decoys give predictive analytics of attacker activity early on in the reconnaissance phase of the kill chain.
For example, decoy Amazon S3 buckets incorporating the company’s name can identify attempted reconnaissance, while decoy UAT, staging and testbed subdomains can identify attackers looking for a weak way in. Decoy login portals / webmail systems / VPNs can also reliably uncover spear-phished credentials (attackers need somewhere to use them). More business-specific use cases include decoy credit cards with a specific bank BIN or fake insurance policyholder information that may be targeted at renewal time.
The use of deception lets less mature companies create rather than consume threat intelligence that is specifically relevant to their vertical or geography. More advanced security teams can leverage advanced counterintelligence deception use cases, such as decoy social media accounts to attract spear-phishing.
Deception + Network Traffic Analysis
Network threat detection is a critical piece of the puzzle, especially since attackers cannot avoid using the network to move around. However, network threat analytics tools suffer from scalability challenges in deployment and are increasingly blind as more traffic is encrypted, even east-west in the network.
Network deception is the ‘original honeypot’, and it still works exceptionally well at detecting everything from worm-like activity such as network-driven ransomware to targeted attackers in large networks.
Through improvements in virtualization and software-defined networking, we can place network decoys at scale in every subnet and VLAN, as well as in the dark IP space of the network to efficiently detect network-driven threats. Moreover, since the network decoy itself is instrumented, it is not blind to encrypted traffic and can provide full packet forensics about the threat.
Deception + Threat Hunting Platform
Deception and threat hunting are two pillars of ‘active defence’ — proactively attempting to take the fight to the adversary. We find that the champions for deception technology at many of our customers are the threat hunting teams, as they are able to think like the attacker and deploy deception in paths where they perceive they will have to traverse.
A deception alert is a perfect trigger to a hunt mission and can let an analyst ring-fence a potential incident with decoys while they pivot on available data to understand the root cause of the threat. The real-world analogy of a hunter laying traps is extremely applicable here.
In fact, we’re so bullish about this use case that we’ve put our money where our mouth is by launching Shadowhunt, a human-driven managed threat hunting service powered by the IllusionBLACK platform.
What can Deception Technology do for You?
Wow, that was a lot of reading you got done. Phew! If you’ve come this far, I’d like to leave you with some closing thoughts. Whether you’re a CISO trying to move the needle on the detect, know, and respond metrics, or someone on the security team struggling to reign in all those false positives, deception technology can improve the quality of your life by an order of magnitude.
If you’re a CISO
Deception technology can help you cut down your:
- Mean Time To Detect (MTTD): Dwell time usually spans months. When you strategically lay traps across your network, you leave attackers with very limited room to maneuver. This can cut down your MTTD to near-zero.
- Mean Time To Know (MTTK): Since deception deployments generate fewer and higher-confidence alerts, the attacker’s activity can be studied much more closely, their TTPs fingerprinted, and their intended target identified in minutes instead of days or hours, particularly with a threat hunting team at the console. In fact, we’ve even seen teams achieve this in single-digit minutes for some attacks.
- Mean Time To Respond (MTTR): With the deception deployment in place for a few weeks or months, you can strategise around automated response for known attack types. This frees up man-hours that can then be directed towards defending against more capable adversaries, and other operational requirements.
If you’re on the security team
- Deception deployments do away with perhaps your most pressing pain point – the flood of alerts from all your security tools. Over the years the industry as a whole seems to have come at the needle-in-the-haystack problem saying “Here’s some more hay”. It’s the reason teams miss alerts or tune them out like the OS error dialogues most folks don’t bother reading before dismissing. With deception, you can instead begin with a high-confidence alert and trace it back to the proverbial needle using specific attributes in the SIEM, specific network source, time range, and optionally, a username.
- Once the response for known attack types is automated, it does away with the tedium of analysing alerts that any machine could. The boring stuff is automated, leaving you to focus on matters that actually warrant your attention.
Well, that’s it from us. If you have any questions about deception technology or want to get an expert opinion, feel free to hit us up. We’d love to hear what you’re currently dealing with and help you out.
Continue Reading
The bright side of the DARKSIDE ransomware
By now, you’ve probably been bulldozed with solution briefings, white papers, vendor pitches, and webinar invitations to discuss how this ransomware could have been stopped. We’ll do things a little differently. We’ll of course include our resources at the end of this post, because obviously we don’t want to be left behind. But we’ll first […]By Sudarshan PisupatiRansomware, the limits of prevention, and active defense
We’re almost halfway through 2021, and there seems to be a ransomware resurgence. Or that’s what the headlines will have you believe. On the contrary, the opposite might be true. According to a Sophos survey, ransomware attacks seem to have gone down in 2021. Only 37% of the organizations surveyed have said they experienced a […]By Amir Moin6 takeaways from GOV.UK’s 2021 cybersecurity breaches survey
COVID-19 has impacted security measures like monitoring, fewer organizations are detecting threats, phishing is the most common threat, and more. Includes active defense recommendations.By Amir Moin
- Detect zero-days, APTs, and insider threats
- 10x the detection capabilities with 1/2 the team
- Get started in minutes, fully functional in hours
