For free, of course.
At this point, I’m positive that you’ve heard of MITRE Shield. It’s a new active defense knowledge base released by MITRE – stuff they’ve been implementing for over a decade to engage adversaries and derail attacks. They’ve opened it up to everyone, and for the first time perhaps, the infosec community has a shared vocabulary and framework for actively defending against attacks instead of reacting to them.
I’ve been having conversations about MITRE Shield and Active Defense with CISOs and customers. While some of the conversations are basic and around what is active defense and why does it matter, what I consistently hear from across the board is – “how do we even begin to implement this stuff?” That’s a fair question, but it’s only one part. What more folks aren’t asking is, where do we implement active defenses for the most impact.
I’ve zeroed down on four active defense techniques from the MITRE Shield matrix that address both the questions – how do I get started with this and where should I be building active defenses first. Think of this as a soft launch guide for your Active Defense journey.
I’ve selected techniques based on two factors:
- Should be easy to implement without involving too many teams.
- Should have a very high impact on disrupting adversary actions.
As a result, all four defenses are Active Directory exclusive. Active Directory has become an adversary favorite attack vector. By deploying active defenses in Active Directory, you’ll be able to make great strides in disrupting adversary actions.
Are there any prerequisites?
Only two:
- You must be able to make some minor changes to your Active Directory server.
- You must have access to a test machine. This could be your own machine or one that’s given to you. It would be great if this machine was not network access restricted in any way to maximize engagement.
Let’s dive right in.
MITRE Shield Technique #1 – Decoy Account
MITRE Shield Procedure – DPR002
Plant decoy accounts in your Active Directory. Any interaction with these accounts is a high-confidence indicator of compromise. These accounts will also help you study the adversary’s actions, mislead attackers by putting these accounts in their path during enumeration, and use them to influence the attacker’s actions and next steps.
Step 1 – Use case setup
Set up a decoy account and give it “Domain Admin” privileges. This will make the account interesting to the adversary.
Step 2 – Auditing Setup and Attack Demo
In this video, we focus on detecting the operation. We show how to setup Windows Auditing so that we can capture the appropriate log. We also demonstrate an attack to test if the logs are captured appropriately.
Psuedo-code for detection rule:
If login_activity observed for decoy_account then raise a high priority alert.
MITRE Shield Technique #2 – Decoy Systems and Decoy Content
MITRE Shield Procedures – DPR0022 and DPR0033
Decoy systems are an excellent active defense tool because they act as a target to lure away attackers from legitimate assets. Decoy content could be anything ranging from fake files to browser shortcuts that act as breadcrumbs to point adversaries to decoy systems.
Step 1 – Use Case Setup
In this video, we set up a webserver on our test machine to channel an adversary towards interacting with it. We create a browser shortcut and place it in a publically accessible location on the Active Directory Server to make it easier for the adversary to discover.
Step 2 – Auditing Setup and Attack Demo
We ensure that our web server is logging connections. If an adversary attempts to conduct reconnaissance against this webserver, we should see a logline in the webserver log.
Psuedo-code for detection rule:
If REQUEST observed for /admin then raise a high priority alert.
MITRE Shield Technique #3 – Decoy Credentials
MITRE Shield Procedure – DPR0024
Decoy credentials are fake usernames and passwords that can be planted in a variety of places including in the Active Directory. They act as silent alarms when interacted with and also as a means to delay the attacker.
Step 1 – Use Case Setup
In this video, we create a batch file planted with fake credentials and store it in a publically accessible location on the Active Directory Server to make it easier for the adversary to discover.
Step 2 – Auditing Setup and Attack Demo
In this video, we show how to set up auditing on your test machine to capture attempts to use the credentials against your test machine.
Psuedo-code for detection rule:
If login_event is 4625 AND username is admin
Then raise a high priority alert.
MITRE Shield Technique 4 – Pocket Litter
MITRE Shield Procedure – DPR0052
Pocket litter is an active defense technique used to mislead attackers into thinking that the system and user they’re exploiting are legit. You plant fake documents, browser history, browser sessions, etc. to give adversaries the confidence that they are on the right track.
Step 1 – Use Case Setup
In this video, we will set up a file share on the test machine. We will plant a shortcut to this file share in a publically accessible location on the Active Directory Server to make it easier for the adversary to discover.
Step 2 – Auditing Setup and Attack Demo
In this video, we show how to set up file share auditing on your test machine to capture attempts to access the file share on your machine.
Psuedo-code for detection rule:
If login_event is 5140 AND share_name contains shared_folder_name Then raise a high priority alert.
Why have you chosen the SYSVOL folder in your videos?
These folders are accessible to all users within your environment. Over time, these folders accrue a lot of files and scripts that are interesting to adversaries. We wish to use these folders to misdirect the attacker, should the attacker go browsing through these folders. It is also uncommon for regular users to require to browse through this folder.
Closing Notes
The focus of this guide was to get your mind thinking about active defense. If there’s one thing I’d like you to walk away with, it’s that if any of these defenses trigger an alarm you will have discovered malicious activity for a couple of hours of effort. And it cost you nothing.
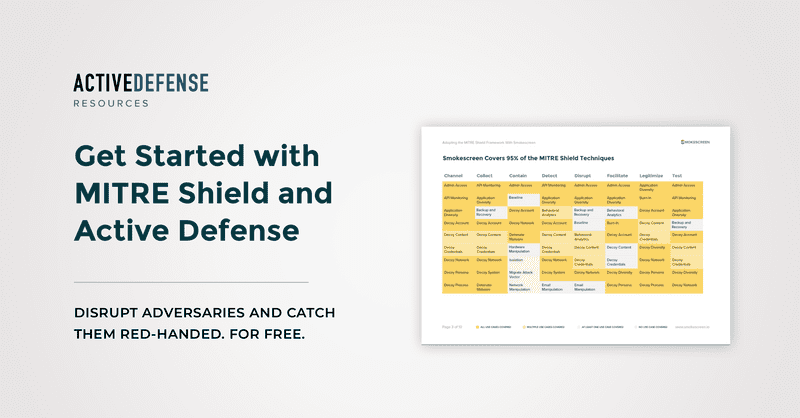
At Smokescreen, we’ve been implementing active defense programs since before it was a thing. No wonder then that Smokescreen covered 95% of MITRE Shield when it launched in Sep 2020. If you’d like to see how we can help, hit us up. Here’s a mapping of Smokescreen to MITRE Shield if it’s helpful.
We’re also running active defense workshops where we deconstruct MITRE Shield and talk about how you can implement it. Feel free to sign up.
Continue Reading
Using deception to shield the insurance sector
Insurance companies are under siege from cyberattacks. We take a look at some of the key pieces of an insurer’s infrastructure the adversaries target and how you can use deception to build active defenses.By Sudarshan PisupatiFinding active defense opportunities in a pentest report
Pentest reports tell a story. By asking why a pentester made certain choices, you can find opportunities to influence attacker behavior and actively defend your network.By Sudarshan PisupatiActive Defense – Incident Response’s New Best Friend
Active defense provides defenders with a shared vocabulary and framework for actively dealing with threats instead of passively reacting to them.By Sudarshan Pisupati
- Detect zero-days, APTs, and insider threats
- 10x the detection capabilities with 1/2 the team
- Get started in minutes, fully functional in hours