By now, you’ve probably been bulldozed with solution briefings, white papers, vendor pitches, and webinar invitations to discuss how this ransomware could have been stopped.
We’ll do things a little differently. We’ll of course include our resources at the end of this post, because obviously we don’t want to be left behind. But we’ll first take you through what we’ve been saying about ransomware these last couple of months. I think it’ll help you understand where we’re coming from and why we recommend dealing with ransomware with a different mindset.
Why we care so much about Ransomware
As a company, we have been vocal about the threat of ransomware for a long time. We’ve seen it singularly wreak more havoc on organizations compared to any other single threat. So we decided to use our social platform to educate the infosec community about ransomware and how to defend against it.
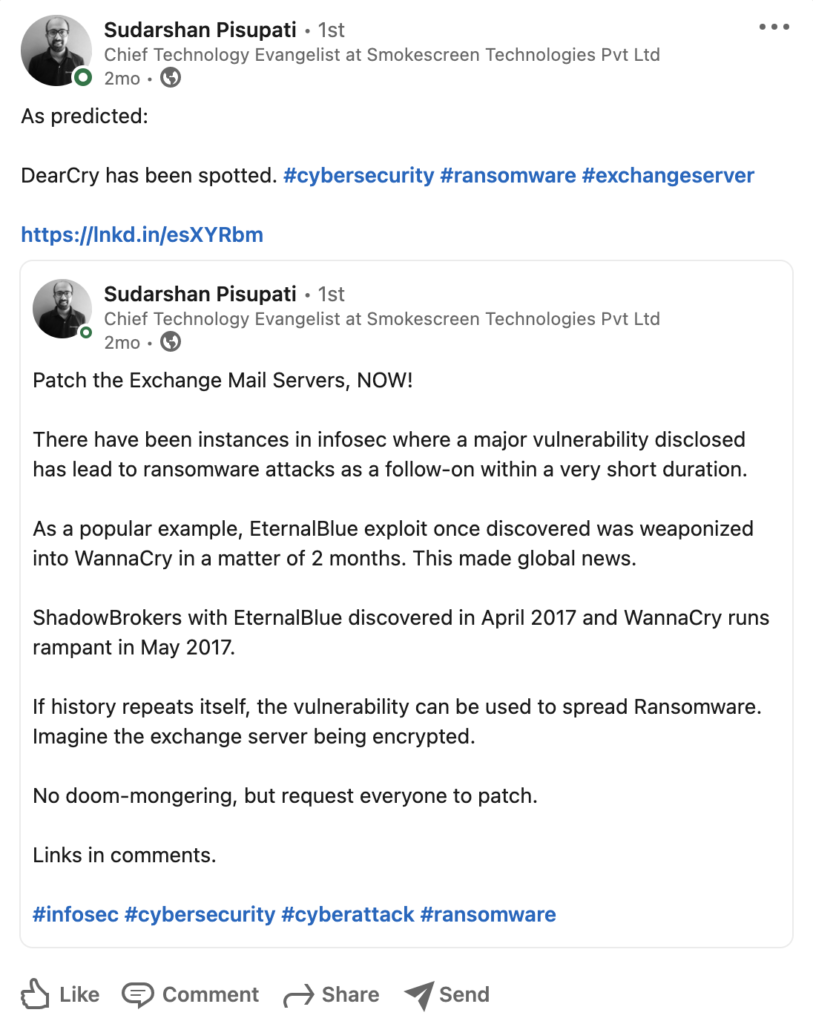
Here’s us predicting the weaponisation of the Exchange vulnerabilities for ransomware ⏱
We even launched a course focussed exclusively on ransomware 🎓
And then we said some more stuff about the impact of ransomware 🎯
We even had a slide just about the consequences of ransomware 💣

And then we wrote a paper on how to defend against it 📝
And made it publically accessible 📖
And then we said this about DARKSIDE 👇🏼
Let me clarify something here – This is not a ‘I told you so’ post. We are not oracles predicting the future. We have been on this trajectory of ransomware making front page news for years now, starting with Wannacry.
But it’s not all doom and gloom.
So what’s the bright side?
The DARKSIDE ransomware did not do anything radically different that can catch the security community off-guard.
We know how most ransomware operates. Download the paper here.
We know what we must do to defend against it.
We simply need to start doing it.
What changes are required to my security program?
Here are three things:
1. Start with “Why”
When analyzing attacker tactics and techniques, ask “Why?”. When you ask “Why?”, it opens up new avenues for guerilla-warfare-style defenses to combat ransomware.
- The Attacker ran Mimikatz. Why? Because they want more credentials. So let’s plant decoy credentials.
- The attacker scanned the network. Why? Because they wanted to find open file shares. So let’s plant decoy file shares.
- The Attacker enumerated AD. Why? Because it’s the phone book of the network. You can find all your targets in Active Directory. So let’s plant decoy entries.
2. Adopt Active Defense-based deception approaches
I’ve enumerated over 40 approaches in the paper on messing with ransomware. Use deception to disrupt what the ransomware is trying to achieve, rather than trying to stop the usage of a specific tool. It’s easy to setup, doesn’t generate too much data, and has a much faster time to value. This statement may look like a vendor marketing plug but it’s not. If you check out MITRE Shield, you will see that the adoption of deception is vital to active defense against a use case like Ransomware.
3. Have a detection strategy that covers key attack surfaces
Reduce reliance on detection in only one part of the network, for example, stacking all the controls on the endpoint. Notice how many EDRs are now talking about XDR? It’s likely because it’s impossible to stop threats meaningfully only in one part of your environment. You need defenses across your environment. Active Defense-based deception does this already.
Irrespective of how you choose to tackle ransomware, here’s the one advise I’ll leave you with 🙏🏼
Continue Reading
Ransomware, the limits of prevention, and active defense
We’re almost halfway through 2021, and there seems to be a ransomware resurgence. Or that’s what the headlines will have you believe. On the contrary, the opposite might be true. According to a Sophos survey, ransomware attacks seem to have gone down in 2021. Only 37% of the organizations surveyed have said they experienced a […]By Amir Moin6 takeaways from GOV.UK’s 2021 cybersecurity breaches survey
COVID-19 has impacted security measures like monitoring, fewer organizations are detecting threats, phishing is the most common threat, and more. Includes active defense recommendations.By Amir MoinUsing deception to shield the insurance sector
Insurance companies are under siege from cyberattacks. We take a look at some of the key pieces of an insurer’s infrastructure the adversaries target and how you can use deception to build active defenses.By Sudarshan Pisupati
- Detect zero-days, APTs, and insider threats
- 10x the detection capabilities with 1/2 the team
- Get started in minutes, fully functional in hours