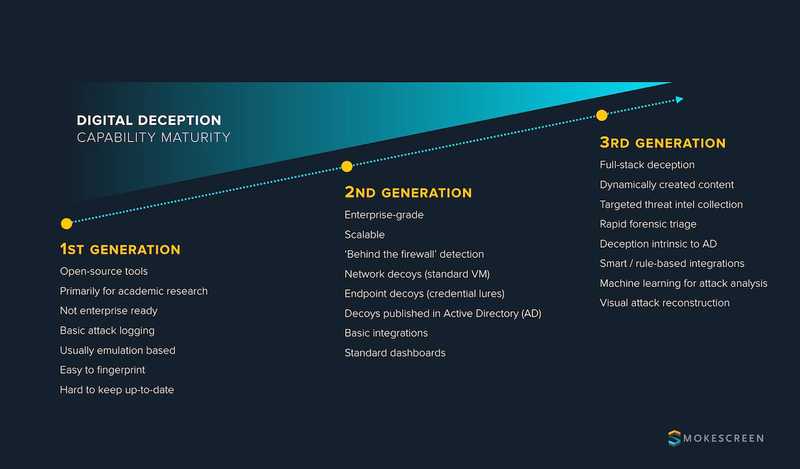
Deception in cybersecurity has come a long way from the early days of the traditional honeypot. We’re currently at 3rd generation deception technology. Recent advances in virtualisation technology and the changing face of modern attacks have led to a rapidly maturing set of deception capabilities that organisations must adopt to see value from deception systems.
When you look at the available deception solutions, there are three clear-cut generations of capability maturity. Here’s how they break down:
1st Generation Deception – The Early Days of Active Defence
Epitomised by the traditional honeypot. This was where much of the early work on building deception platforms began. Much of the available technology is open-source, and has primarily been developed as academic research projects. They are usually emulation based, with basic logging capabilities. Unfortunately, most of these projects are now abandonware as the primary developers have moved on. They’re easy to fingerprint and often have well-known security vulnerabilities. That said, they are quick to setup and play with, and are great for dipping one’s feet into deception or helping to build a business case.
2nd Generation Deception – Bringing Deception to the Enterprise
A few years ago, commercial solutions appeared that try to reboot the network honeypot with enterprise features such as central monitoring and alerting. They typically run a few full ‘fat’ virtual machines that are propagated via NIC bonding / IP aliasing to distribute these VM’s across the enterprise network. They’ll often include some form of lure on the endpoint to draw attackers towards the VMs. These are essentially ‘enterprise honeypots’, however they are technology limited as they rely on the same few VM’s to create multiple decoys — something that won’t fool a seasoned cyber-criminal, leave alone a nation-state attacker.
3rd Generation Deception Technology – The State-of-the-Art in Proactive Defence
3rd generation deception technology represent the state-of-the-art in terms of technology adoption. Using technology such as micro-virtualisation to replace fat VM’s, means you can have hundreds of individually unique network decoys, each with their own personality. 3rd gen systems also incorporate advanced analytics, machine learning, automated data creation for at-scale deployments, and visual attack reconstructions. They have coverage of areas that the network honeypot misses, including support for threat intelligence decoys, web-application integrations, social-engineering attacks, and Active Directory attacks. Often, they will incorporate orchestration as a first-class citizen — integrating with other solutions through rule-based triggers.
Each generation builds on the next, and we’re likely to see far more innovation in the deception space in the next 12 to 24 months. At Smokescreen, we’ve got an extremely deep innovation roadmap, with a lot of new stuff in the lab that we’ve been beta-testing with mature customers for a while now. Many of these new capabilities are completely novel, and really brings active defence to defence teams, letting them go toe-to-toe with apex adversaries.
Continue Reading
6 takeaways from GOV.UK’s 2021 cybersecurity breaches survey
COVID-19 has impacted security measures like monitoring, fewer organizations are detecting threats, phishing is the most common threat, and more. Includes active defense recommendations.By Amir MoinUsing deception to shield the insurance sector
Insurance companies are under siege from cyberattacks. We take a look at some of the key pieces of an insurer’s infrastructure the adversaries target and how you can use deception to build active defenses.By Sudarshan PisupatiYou Need Deception Technology. And It’s Not Why You Think
Deception technology is a different way of thinking about cybersecurity. Without it, attackers have the advantage. You can take that advantage back.By Kevin Fiscus
- Detect zero-days, APTs, and insider threats
- 10x the detection capabilities with 1/2 the team
- Get started in minutes, fully functional in hours